Compiling Linux Exploit Code and Tools in Windows using Cygwin
Many of the best security tools are released for Linux and of Unix like operating system and may be ported to Windows much later if at all. Also, many times sample exploit code is written to be compiled in Linux using GCC, even if the target attack platform is Windows. The best way to use these exploits/tools is to learn Linux and install it on your workstation, but for those who are forced to use Windows NT/200/XP or who want portable binaries they can run from other's Windows boxes there is an alternative: Cygwin ( http://www.cygwin.com/ ).
What is Cygwin you might ask? From their website:
* Cygwin is a Linux-like environment for Windows. It consists of two parts: A DLL (cygwin1.dll) which acts as a Linux emulation layer providing substantial Linux API functionality.
* A collection of tools, which provide Linux look and feel.
This tutorial will show you how to take an exploit written for *nix and compile it to work under Windows.
Step 1. Download the Cygwin setup executable from http://www.cygwin.com/ and run it. This will bring up a copyright screen, just click next. (screenshot)
Step 2. Choose "Install from Internet." Click the next button. (screenshot)
Step 3. Choose a root directory for Cygwin, I normally just let it stay the default, which is "C:\cygwin." Click the next button. (screenshot)
Step 4. Choose a place to put the install files the setup program downloads. Click the next button. (screenshot)
Step 5. Direct connection is most likely what you want to choose on this dialog, unless you are behind a proxy. Click the next button. (screenshot)
Step 6. Choose a mirror that you think may be close to you. Click the next button. (screenshot)
Step 7. The next dialog lets us choose the packages we want to install. Which packages you need depends are what you are compiling. For this demo just accept the default packages and then scroll down the list to add "cmake", "gcc: C compiler" and "gcc-g++: GCC C++ compiler" by clicking where it says "Skip" to change it to a version number. Click the next button. (screenshot A, screenshot B )
Step 8. Your packages will begin downloading, click next when they are finished. (screenshot)
Step 9. Once the packages have all been downloaded a screen will pop up asking if you want to add icons for Cygwin to your Desktop and Start Menu. Accept the defaults and choose finish. (screenshot)
Step 10. For our test we will download a simple exploit and save it into the Cygwin folder (c:\cygwin\ if you took the defaults). For my tutorial I will be using the HP Printer Display Hack available here: http://irongeek.com/downloads/hpunix.c
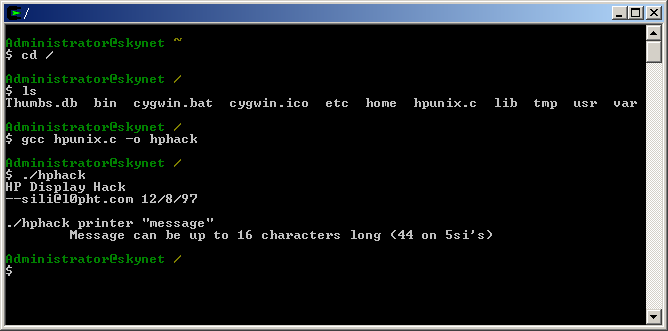
Step 11. Find the Cygwin shortcut on your desktop and double click it. Once it comes up you should see a shell prompt. issue the "cd /" command to take you to the root of your Cygwin install, bring up a directory listing using the "ls" command to make sure the c file is there then issue the command "gcc hpunix.c -o hphack" to create your binary. The string after the "-o" parameter tells the compiler to name the binary hphack.exe. The binary can now be ran with just the "./hphack" command.
Once you have compiled your exploit/tool you no longer need the rest of the Cygwin environment, just copy the binary (the exe file) you created to a disk or USB thumb drive and then copy the file "cygwin1.dll" (in c:\cygwin\bin\cygwin1.dll if you took the defaults) to the same directory or somewhere in the path. Now you should be able to run the executable from just about any Window box you encounter.