| ||||||||||
|
| ||||||||||
|
Search Irongeek.com:  
Help Irongeek.com pay for bandwidth and research equipment: |
Config: DHCP Warning: Updated for OZ 3.5.3 opie-wellenreiter_1.2.0-r1_arm.ipk Make sure you get 1.2.0-r1 and not
1.2.0-r0 as r0 seems to have issues with some of the other WiFi
software on the ROM (some sort of version conflict between We V16 and
We V17). To install just change to the directory the package is in and
use the two following commands: ipkg -d
ram install opie-wellenreiter_1.2.0-r1_arm.ipk You may have to restart your Zaurus
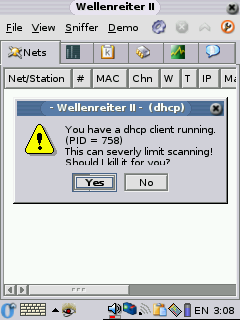
after the install to get the icons to appear. When you first run it
give Wellenreiter II a few seconds so it will pop up the message
about killing the DHCP client, once DHCP is killed it works a lot
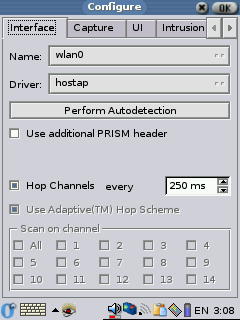
better. Make sure you choose the proper card under the config page, in
my case wlan0 (I have a TRENDware TE-CF100, if I choose WiFi0 there are
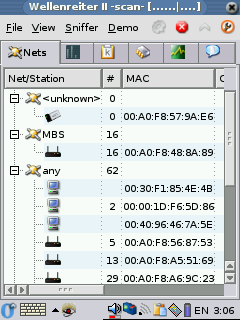
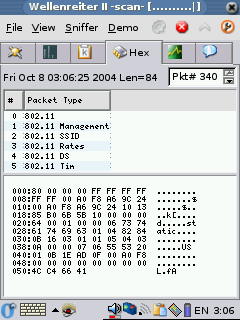
no errors, but no WAPs are ever found either). Wellenreiter II can
tell you what WAPs it finds, some of the clients, the signal strength
and information about the packets it sees. Wellenreiter II can also
generate a capture dump file that you can later open up in Ethereal on
your pc and see much of the traffic on multiple Waps and SSIDs. It's a
pretty kick ass tool. Updated for OZ 3.5.3 2005-06-R1 These instructions should help you get Kismet 2005-06-R1
working on your Zaurus. First we need to install Ncurses support to get
rid of errors like "Error opening terminal: xterm." To install ncurses
get ncurses_5.4-r7_arm.ipk and ncurses-terminfo_5.4-r7_arm.ipk
from the OZ 3.5.3 feed and libstdc++6_4.0.1-3_arm.deb from the Debian
packages site (http://packages.debian.org/unstable/libs/libstdc++6)
, then use these commands to install them: ipkg -d
ram install ncurses_5.4-r7_arm.ipk ipkg -d
ram install libstdc\+\+6_4.0.1-3_arm.deb Now we can install Kismet, you can get the deb file for
it from the Debian packages site (http://packages.debian.org/unstable/net/kismet)
Use these commands to install it: ipkg
--force-depends -d ram install kismet_2005.06.R1-1_arm.deb SIDE NOTE: Now we will have to do some file editing.
I'm a lamer so I don't use the vi package that comes already installed,
I use Nano.You can find Nano in the OZ 3.5.3 feed or at my archive.
It's very easy to install: ipkg -d
ram install nano_1.3.5-r0_arm.ipk Once you have installed Kismet edit the old kismet.conf
(/mnt/ram/usr/local/etc/kismet.conf , it could be in a different path
depending on where you installed it) to reflect the proper source
setting, for my Replace: source=none,none,addme With: source=hostap,wlan0,hostap While your at it, it may be a good idea to change where
Kismet dumps log files. This could be useful if you want to dump a lot
of packets to a dump file so you can look at them in Ethereal on your
PC later. In my case, I just wrote them to the RAM mount: Replace: logtemplate=/var/log/kismet/%n-%d-%i.%l With: logtemplate=/mnt/ram/%n-%d-%i.%l If you have a Prism2 card you may just want to use my conf
file: kismet.conf. Basically all I
did was tell it to use hostap as the source, you may have to make some
changes if you don't use a Prism based card. Look for the "source="
setting, some possible choices might be: source=prism2,wlan0,prism2source Next edit the kismet script (/mnt/ram/packages/usr/bin/kismet
if you installed it to ram) and add the following lines right after
"#!/bin/sh" export TERMINFO=/usr/share/terminfo Or you can jus copy of my kismet script here. Now all you should have to do is drop
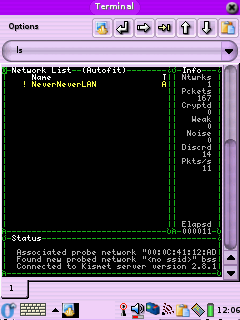
out to Opie Terminal and type: kismet You should now see the Kismet interface we all know and love.
After running Kismet you should see log files in /root with names like: Kismet-*-1.gps These are basically logs of all the APs you have found, but
the dump file is something special. The dump file contains captured
packets from the networks Kismet has detected, it's in TCPDump format
and can be loaded into other tools like TCPDump, Ethereal and Ettercap
to find out more information about what's running on the network the
packets were captured from. Don't forget to delete these files if you
start to run out of space on your Zaurus. Thanks to Dave Dmytriw and this thread:
15 most recent posts on Irongeek.com:
| |||||||||
If you would like to republish one of the articles from this site on your
webpage or print journal please contact IronGeek.
Copyright 2020, IronGeek
Louisville / Kentuckiana Information Security Enthusiast
 Printable version of this article
Printable version of this article