Sniffers
DSniff
Updated for OZ 3.5.3
Website:
http://www.monkey.org/~dugsong/dsniff/
DSniff is a great little sniffing package from Dug Song. The DSniff
binary itself parses out passwords from the traffic is sees on the
network. Some of the protocols it supports include smtp, pop3, http
basic and can break ssh and ssl by proxying the connection. The package
also comes along with the binaries arpspoof, filesnarf, mailsnarf,
msgsnarf, urlsnarf, and webspy. So far I've only tested the Dsniff
binary with a standard ethernet card, but it seems to work. I
downloaded the Debian ARM packages from
http://packages.debian.org/unstable/net/ but you can copy them from
my mirror if you wish. You will need the download the files and use the
following commands:
1. Install the needed libraries and the Dsniff package and link them
into the root file system, in my case I'm installing from my SD card. I
got my packages from the Debian unstable branch, but you could get them
from the mirror:
ipkg --force-depends -d ram install
libnet1_1.1.2.1-2_arm.deb
ipkg-link add libnet1
ipkg --force-depends -d ram install dsniff_2.4b1-12_arm.deb
Since I was attached to the Internet via Wi-Fi at the time it
automatically got libice6, libsm6 and openssl from the OpenZaurus feed.
Then I had some more linking to do:
ipkg-link add dsniff
ln /usr/lib/libnet.so.1 /usr/lib/libnids.so.1.20
ipkg --force-depends -d ram install libdb4.2_4.2.52-19_arm.deb
ipkg-link add libdb4.2
ipkg --force-depends -d ram install libnids1.20_1.20-3_arm.deb
ipkg-link add libnids1.20
2. Next just start Dsniff, don't forget to specify an interface. On
my Zaurus, to specify the TE-CF100 10/100 Ethernet card I use the
following command when starting DSniff:
dsniff -i eth0
To use my WiFi card I you use the following command:
dsniff -i wlan0
I've had problems seeing traffic on my wireless LAN, e-mail me and
let me know if the apps work for you. Special thanks to Cowboy and Mark
McLaughlin for the help and encouragement in this section.
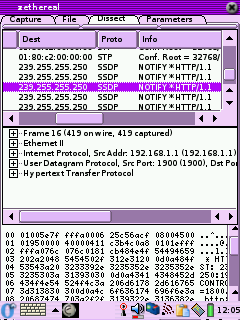 Zethereal
Zethereal
Website:
http://www.cartel-securite.fr/pbiondi/zaurus/zethereal.html
Major Update:1-27-2004
Zethereal is Ethereal for the Zaurus. It's a good little
sniffer/protocol analyzer. All the binaries I've found for it are
compiled with the old gcc so you will have to use the compatibility libraries.
Make sure you have installed LibPcap then install the ipk in my mirror
(provided by Dan L). You will also need to install libglib (my mirror of libglib,
boosted from Debian) and do some symlinking to get it toy work, I
installed it from the SD card as follows:
| |
ipkg -force-depends -d ram install
/mnt/card/libglib1.2_1.2.10-9_arm.ipk
cd /usr/lib/
ln -s /mnt/ram/usr/lib/libglib-1.2.so.0
ln -s /mnt/ram/usr/lib/libglib-1.2.so.0.0.10
ln -s /mnt/ram/usr/lib/libgmodule-1.2.so.0
ln -s /mnt/ram/usr/lib/libgmodule-1.2.so.0.0.10
ln -s /mnt/ram/usr/lib/libgthread-1.2.so.0
ln -s /mnt/ram/usr/lib/libgthread-1.2.so.0.0.10
|
Since this was created with the old gcc you will have to edit the
.desktop file:
nano
/opt/Qtopia/apps/Applications/zethereal.desktop
and change the exec line to read:
Exec=runcompat zethereal-1.0-arm
Restart Opie and it should all work. By the way, if for some reason
installing the IPK does not put icons in the GUI do the following:
ln -s
/mnt/ram/usr/bin/zethereal-1.0-arm /usr/bin/
ln -s /mnt/ram/opt/QtPalmtop/pics/zethereal.png /opt/QtPalmtop/pics/
ln -s /mnt/ram/opt/QtPalmtop/apps/Applications/zethereal.desktop
/opt/QtPalmtop/apps/Applications/
then restart Opie.
Update 6/20/2005: M Delroy sent in the following information
on what he had to do to get Zethereal running on OZ 3.5.3:
Getting Zethereal-1.0-arm Running on OpenZaurus 3.5.3
First install libqt_mt3_3.3.3-r5_arm.ipk
It must be installed into ram.
To do so save the file to the sd card. With OpenZaurus 3.5.3, when
transferred a *ipkg file via syncing from Qtopia 1.7 on Windows the
file is saved to /media/card/Documents/application/ipkg
Issue the following command to install libqt_mt3_3.3.3-r5_arm.ipk in
the directory it is saved in.
ipkg –force-depends –d ram install libqt_mt3_3.3.3-r5_arm.ipk
<enter>
Next create a link with
ipkg-link add libqt_mt3_3.3.3-r5_arm.ipk <enter>
Now install task-opie-minimal_1.0.3_arm.ipk with the following
ipkg -force-depends –d ram install task-opie-minimal_1.0.3_arm.ipk
<enter>
There is no need for a ipkg-link with task-opie-minimal_1.0.3_arm.ipk
Install opie-sh_1.2.0-r0_arm.ipk with
ipkg -force-depends –d ram install opie-sh_1.2.0-r0_arm.ipk
<enter>
Next create a link with
ipkg-link add opie-sh <enter>
We now need to install libpcap0.8_0.8.3-r0_arm.ipk with the following
ipkg -force-depends –d ram install libpcap0.8_0.8.3-r0_arm.ipk
<enter>
No ipkg-link is needed.
Now install libpcap0_0.7.2_arm.ipk with
ipkg -force-depends –d ram install libpcap0_0.7.2_arm.ipk <enter>
This installs the libpcap0_0.7.2 files into /media/ram/packages/usr/lib
However, OpenZaurus needs links located in /usr/lib to the files in
/medial/ram/packages/usr/lib Create the links with the following:
Cd into /media/ram/packages/usr/lib and make sure libpcap0_0.7 files
are located there.
Cd into /usr/lib and issue the following command for each
libpcap0_0.7.2 file
ln -s /media/ram/packages/usr/lib/”libpcap0_0.7.2 file name”
<enter>
Reboot and make sure the links are still in place.
There is no need for ipkg-links with libpcap0_0.7.2
To work around the quickexec not found error when installing
sharp-compat-libs we need to do the following:
Cd into /media/ram/packages/etc/init.d/ and see if quickexec is there.
To create a link to /media/ram/packages/etc/init.d/quickexec in
/etc/init.d issue the following command
ln -s /media/ram/packages/etc/init.d/quickexec /etc/init.d <enter>
Now install sharp-compat-libs_0.5-r2_arm.ipk with the following
ipkg -force-depends –d ram install sharp-compat-libs_0.5-r2_arm.ipk
<enter>
Now cd into /etc/init.d and delete the link to quickexec
Create a link for sharp-compat-libs with the following command
ipkg-link add sharp-compat-libs <enter>
Install libglib_1.2.0_arm.ipk with the following
ipkg -force-depends –d ram install libglib_1.2.0_arm.ipk <enter>
This installs libglib_1.2.0 files to
/media/ram/packages/home/root/usr/lib/ However OpenZaurus needs links
to these files located in /usr/lib
Cd into /media/ram/packages/home/root/usr/lib/ and make sure that there
are libglib_1.2.0 files located there. The following files should be
present.
libglib-1.2.so.0
libglib-1.2.so.0.0.10
libgmodule-1.2.so.0
libgmodule-1.2.so.0.0.10
Create the links by cding into /usr/lib and issue the following for
each libglib_1.2.0:
ln –s /media/ram/packages/home/root/usr/lib/”libglib_1.2.0 file name”
Such as
ln -s /media/ram/packages/usr/lib/libglib-1.2.so.0
ln -s /media/ram/packages/usr/lib/libglib-1.2.so.0.0.10
ln -s /media/ram/packages/usr/lib/libgmodule-1.2.so.0
ln -s /media/ram/packages/usr/lib/libgmodule-1.2.so.0.0.10
We still need libglibthread files so Install
libglib1.2_1.2.10-9_arm.ipk by doing the following
ipkg -force-depends –d ram install libglib1.2_1.2.10-9_arm.ipk
<enter>
This installs libglib1.2_1.2.10-9 files to /media/ram/packages/usr/lib
However OpenZaurus needs links in /usr/lib to the files in the
/media/ram/packages/usr/lib location
Cd into /media/ram/packages/usr/lib and confirm that the following
files are located there:
libgthread-1.2.so.0
libgthread-1.2.so.0.0.10
cd into /usr/lib and create links for the libglibthread files with the
following commands
ln -s /media/ram/packages/usr/lib/libgthread-1.2.so.0
ln -s /media/ram/packages/usr/lib/libgthread-1.2.so.0.0.10
Reboot and make sure the links in /usr/lib are still present.
You can now install zethereal_1.0_arm.ipk with the following command
ipkg -force-depends –d ram install zethereal_1.0_arm.ipk <enter>
Create a link for zethereal with
ipkg-link add zethereal-1.0 <enter>
Reboot and follow the instructions at
http://opie.handhelds.org/cgi-bin/moin.cgi/oz_2dcompat_20HowTo
On how to start Zethereal using the oz-compat (sharp-compat libraries).
Note: Zethereal did not appear to function with new libglibs and
libpcap so use the versions mentioned in this document.
When using zethereal you may find that it starts more reliably via the
zethereal-1.0-arm command rather then the icon.
Zethereal does not place the nic in monitor mode. To place the nic in
monitor mode you may need to first open zethereal via the
zethereal-1.0-arm command. Then without closing zethereal open a second
console session and issue the following command
ifconfig wlan0 down
iwpriv wlan0 monitor 2 x <enter>
where x=the channel you wish to monitor
Check that the nic is truly in by issuing
iwpriv wlan0|more <enter>
You should see monitor mentioned in the output
Bring the nic up with the ifconfig wlan0 up command. Close this console
session and re-enter zethereal.
Under the capture tab make sure that wlan0 is chosen for the nic, enter
a maximum number of packets, and click start.
Note: The packet view under the dissect tab does not update in real
time. When the capture completes or after you click stop re-entering
the dissect tab will show the packets captured. |


 Zethereal
Zethereal
 Printable version of this article
Printable version of this article