| ||||||||
|
| ||||||||
|
Search Irongeek.com:  
Help Irongeek.com pay for bandwidth and research equipment: |
Updated for OZ 3.5.3 The only version on Nmap I have found that
has be directly ported to the Zaurus is 3.27, but you can get the newer
Debian ARM packages (available here:
http://packages.debian.org/unstable/net/nmap ) to function with a
little work. I'll be using version 3.93-1, which I have at my mirror.
Download the following files: Following these step by step instructions
to install Nmap 3.81-2 on your Zaurus. All of them can be performed by
secure shelling into your Zaurus or using the keypad at the Opie
Terminal window: 1. Copy the five files listed above (in red) to a CF or SD card (I
will use the CF card in my examples). Insert the card then change
directories into whatever card you put them on. cd /mnt/cf/ 2. Install libcrypto and link it: ipkg -d ram
install libcrypto0.9.7_0.9.7e-r1_arm.ipk Ignore any errors as long as it says "Successfully done" at the end. 3. Install libssl and link it: ipkg -d ram
install libssl0.9.7_0.9.7e-r1_arm.ipk Ignore any errors as long as it says "Successfully done" at the end. 4. Install libstdc++5 and libstdc++6 and link them: ipkg
--force-depends -d ram install libstdc\+\+5_3.3.6-10_arm.deb ipkg
--force-depends -d ram install libstdc\+\+6_4.0.2-2_arm.deb Ignore any errors as long as it says "Successfully done" at the end. 4.5. If you installed the OZ version of pcre to get
Konqueror to work remove it: ipkg remove pcre Otherwise just go to step 5. 5. Install libcre3 and link it: 5.5. If you
installed the OZ version of pcre to get Konqueror to work (or plan to
install it later) symlink libpcre so Konqueror can find it:
You can find the full man page for Nmap at http://www.insecure.org/nmap/data/nmap_manpage.html
but here are a few useful flags: -P0 Don't ping first, this is useful because a lot of
hosts turn of ICMP echo requests now. -O Do an OS detection -e Specify and interface (eth0, wlan0, etc) -sV Version scan, find out the version of the
daemon that's listening on an open port. -A Does the same thing as doing a -O and -sV at
the same time. This switch may do some other things in the future, ask
Fyodor. :) Also check out my videos:
http://www.irongeek.com/i.php?page=videos/nmap1 From: Mark Owen [mailto:mr.markowen@gmail.com] Don't know if this will be of any use to anyone but I have THC-Hydra is a dictionary attack application that supports
TELNET, FTP, HTTP, HTTPS, HTTP-PROXY, LDAP, SMB, SMBNT, MS-SQL, MYSQL,
REXEC, CVS, SNMP, SMTP-AUTH, SOCKS5, VNC, POP3, IMAP, NNTP, PCNFS,
ICQ, SAP/R3, Cisco auth, Cisco enable, and Cisco AAA
(incorporated in telnet module). I am going to use it for testing in-house servers and
password vulnerability demonstration to clients. I
recommend it for only LEGAL USE AS USING IT OTHERWISE CAN GET YOU IN
SERIOUS TROUBLE! It required a little sym linking but it works rather
well overall. The program's site is at http://thc.org/thc-hydra/
I've created the following step by step howto on its installation.
It requires libssh, libssl-dev, and libssl to run correctly. This
howto expects you to know how to download and install them. Just run the following commands to successfully install
it. cd wget
http://thc.org/thc-hydra/hydra-4.5-arm.tar.gz gunzip hydra-4.5-arm.tar.gz tar xvf hydra-4.5-arm.tar cd hydra-4.5-arm ipkg install libssh_0.1_arm.ipk #Could
not find in feed but includedin download ln -s /usr/lib/libssl.so.0.9.7
/usr/lib/libssl.so.0.9.6 ln -s /usr/lib/libcrypto.so.0.9.7
/usr/lib/libcrypto.so.0.9.6 echo /lib/libgcc_s.so.1 >
/etc/ld.so.preload ipkg install hydra_4.5_arm.ipk hydra -h #DONE! If you have any problems feel free to e-mail me back. Mark Owen Updated for OZ 3.5.1 Nemesis is packet injection utility.
It allows you to spoof other hosts and generally cause confusion on the
network. I just took the Debian ARM packages and renamed them with a
.ipk on the end. The package comes with the following utilitys: nemesis-arp I wanted to get the newest package I could find
(nemesis_1.32+1.4beta3-2_arm.deb) to work but I can't find a version on
Libnet0 that I can install on my Zaurus. I decided to use the older
version, 1.32-5. To install from the CF card do the following commands: ipkg -force-depends -d ram install
/mnt/cf/nemesis_1.32-5_arm.ipk then symlink everything someplace in you path: ln -s /mnt/ram/usr/sbin/n* /bin/ Since the libpcap libray files have a different name in OZ
3.5.1 we have to do the following symlink so nemesis can find it: ln -s /usr/lib/libpcap.so.0.7
/usr/lib/libpcap.so.0 One cool use is to fake out an IDS system. If I used the
command nemesis-tcp -x 1025 -y 22 -S
207.46.134.157 -D 192.168.240.7 it would make it look as if Microsoft.com was attacking the
target host. Here is a example of a script I wrote that can be used to
make it look like another host is doing a port scan: for port in 21 22 23 25 80 138 139 6776 10008 31337 copy all that into a text file, chmod +x it and use it by
issuing a command like frame.sh Farmed_ip Target_IP You will most likely want to change your MAC address first. A note on modems and wardialing from a Zaurus: Knightmare sent me some notes on wardialing from the Zaurus, and since I had
no better category to post them in I'll put them here: | |||||||
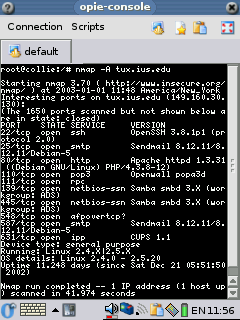 Nmap
Nmap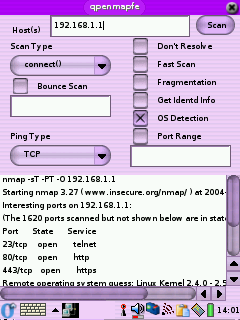 Or you can also download libssl0.9.7_0.9.7e-r1_arm.ipk and libcrypto0.9.7_0.9.7e-r1_arm.ipk from the
OpenZaurus feed at
Or you can also download libssl0.9.7_0.9.7e-r1_arm.ipk and libcrypto0.9.7_0.9.7e-r1_arm.ipk from the
OpenZaurus feed at