Hardware Key Logging Part 1:
An Overview Of USB Hardware Keyloggers,
And A Review Of The KeyCarbon USB Home Mini
 There are a lot of software keyloggers available, and I have even done some work on one.
This article however is on hardware keyloggers, specifically those that work
with USB keyboards. While the PS/2 keyboard may still be more popular, it seems to me
that it's on
its way out so I thought covering USB keyloggers would be more useful. If I ever
get the hardware and time, I may cover PS/2 loggers as well.
There are a lot of software keyloggers available, and I have even done some work on one.
This article however is on hardware keyloggers, specifically those that work
with USB keyboards. While the PS/2 keyboard may still be more popular, it seems to me
that it's on
its way out so I thought covering USB keyloggers would be more useful. If I ever
get the hardware and time, I may cover PS/2 loggers as well.
Hardware keyloggers fill a few niches:
Uses/Target Audience
1. Writers: Users can install them on their own systems as a backup for the work they've typed. My personal feeling is this is not the most practical use. Maybe if you type in long continuous strings and rarely copy and paste or backspace over mistakes it would work well for you. Because of the way I work on my articles I doubt it would be very useful to me since my writing style is hardly linear. I go back over the same article many times making little changes here and there, making the key log rather unreadable. However, if you are a better typist than I, and your thought processes more coherent, this form of backup may work for you.2. Businesses: Some companies may use keyloggers for monitoring employees for misconduct. At the high price tag of many hardware keyloggers, this is probably the major market for them. In my opinion large companies might be better off rolling out a custom software keylogger via a GPO since it can give much greater detail about when and in what application the keystrokes were made. Only the highest end hardware keyloggers support time/date stamping, and even then they can't tell you in what application or context the typing was made. If you were doing a serious investigation into misconduct, time/date stamping would be a must. The keylogger I'll be reviewing in this article does not have these time/date stamping features, but the same vendor does sell higher end models that do.
3. Parents: Some parents may choose to use a hardware keylogger to monitor their kids. My thoughts on the subject are that parents would be better served by using filtering software, since the kid does not have to be very bright to just physically remove a hardware keylogger if they know it's installed.
4. Pen-testers/Crackers/Spies: If an attacker is trying to get someone else's password or proprietary information hardware keyloggers can come in quite handy. The high price tag and difficulty of gaining physical access to the monitored machines may limit this use to only internal corporate spies and well financed tiger teams, but it's still a valid use.
Now that your
aware of why someone might want to use a hardware keylogger I'll cover some of
their pros and cons.
Since I'm a negative sort of person, I'll cover the downside of hardware vs.
software keyloggers first:
Disadvantages
1. There's no chance of emailing or grabbing the keystroke logs from over a network; the device has to be physically recovered to obtain the logs. Having to have physical access can be a serious obstacle to installing and retrieving the keylogger.2. The hardware keylogger gives little to no information on what app was active when the keystrokes happened. With out knowing the context of the keystrokes it's much harder to tell if a string of characters is from a document, an IM session or a password.
3. Hardware keyloggers are rather expensive. One of the cheaper USB models I've found was $79.99; the one I'm reviewing from KeyCarbon is $189 - and it's not even the higher end model.
4. If found, external hardware keyloggers are much easier to remove than software keyloggers. You just pluck them off the keyboard's cord. Removing software keyloggers depends on the users privilege level, or how knowledgeable they are about how to gain a higher privilege level. ☺
Now for the positives:
Advantages
1. Most software keyloggers are detected by anti-malware apps. Depending on which software package is used, the anti-virus system will likely detect the keylogger and remove it, or at the very least report it to the user. Hardware keyloggers, on the other hand, are very hard to detect without physical inspection. That's not to say it's impossible, and I'll write more on that subject a little later in this article.2. Hardware keystroke loggers can get keystrokes from before the OS is even loaded (hello bios password), or from around software that limits what processes can access the keystrokes (like the Windows GINA logon after the old three finger salute of Ctrl-Alt-Del).
3. Hardware keyloggers can support logging of almost any OS, as long as the keyboard is a fairly standard USB HID (Human Interface Device). Windows, Linux, Mac OS X - it makes little difference to a hardware keylogger.
Now that I've given you an overview of hardware keyloggers, let's get to the review.
KeyCarbon USB Home Mini Review
 I sent out a request for review units from some of the
major manufactures
of USB keyloggers. The first to respond was BitForensics, with an example of
their KeyCarbon USB Home Mini (KCU401). BitForensics bought the makers of the
KeyPhantom in 2006 and updated the product into the current KeyCarbon line of
keyloggers. The product page for the unit I'm testing can be found at:
I sent out a request for review units from some of the
major manufactures
of USB keyloggers. The first to respond was BitForensics, with an example of
their KeyCarbon USB Home Mini (KCU401). BitForensics bought the makers of the
KeyPhantom in 2006 and updated the product into the current KeyCarbon line of
keyloggers. The product page for the unit I'm testing can be found at:
 http://www.keycarbon.com/products/keycarbon_usb/overview/
http://www.keycarbon.com/products/keycarbon_usb/overview/
The KeyCarbon has a flashable firmware (I reviewed with v2.3.0.5020) so it can be updated as problematic keyboards come
out, and has 512KB of nonvolatile memory for storing keystrokes. At first, 512KB
or memory may not sound like much when we compare it to today's multi-gigabyte
flash drives, but 512KB is a lot of typing. If the 512KB limit is reached
the KeyCarbon will keep the newest 512KB of keystrokes and dump the oldest
ones.
The first thing I get
asked by people when I tell them about hardware keyloggers is "Won't people
see them"? The answer to that questions is "it depends", if you have the same
rats' nest of wires and the dust-lepus that I have, then I doubt it! The
KeyCarbon is quite a bit smaller than the KeyPhantom, so if it's placed right it
should go unnoticed. Check out
BitForensics' site for internal PCI/Mini PCI
hardware keyloggers if you're a corporate user that wants something even more
stealthy.
Installation is simple, just plug the keylogger inline with the keyboard. The
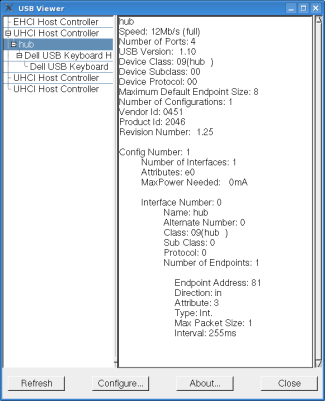
system should detect the KeyCarbon USB Home Mini as a hub device with a vendor id of 0451
and a product id of 2046. I checked out these identifiers on the Linux USB site:
http://www.linux-usb.org/usb.ids
and they correspond to a generic Texas Instruments hub, nothing too conspicuous.
The keyboard you plug into the KeyCarbon shows up as being plugged into the hub.
I've run with it plugged into my home machine for about a week and everything
seemed stable. Really, installation is as simple as just plugging the KeyCarbon
into a USB port, and the keyboard into the KeyCarbon. So far I've tested it in a
USB 1.1 and a USB 2.0 port, and with a Dell sk-8135 rev G USB 1.1 keyboard
and a IBM Model M with a PS/2 to USB adapter. Keep in mind that not all PS/2 to
USB adapters will work in all circumstances. Things can get odd, especially with
the Model M. After conversing with my contact at BitForensics they seem to pride
themselves in having wider compatibility with more USB keyboards then some of
their competitors, and if a problem keyboard is found it may be fixed via a
newer firmware release.
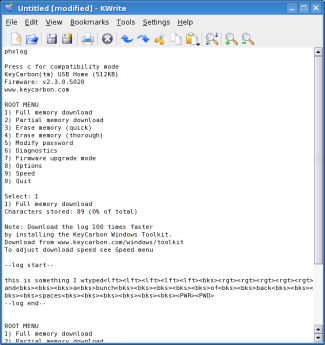
Recovering the keystrokes is also
easy and can be done in one of two ways depending on your operating system. On
all operating systems you can simply open up any text editor (like Notepad or
KWrite), type in the password, ("phxlog" by default) and the KeyCarbon will
bring up a menu as seen in the screenshot. Notice I'm using Linux for this part
of the article; the OS really does not matter as long as it's a standard USB
HID keyboard. All of the root menu options are pretty
straightforward. Type a "1" once the root menu is up and the KeyCarbon will start typing
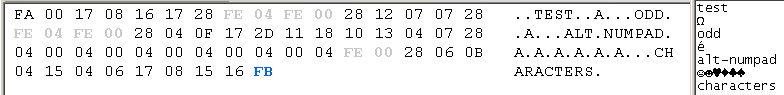
the logged keystrokes into the text file for the user to view. Nifty. You will noticed some
special keywords like "<PWR>" or "<PWD>" from time to time in the
logs. "<PWR>" just means
the USB port the KeyCarbon was plugged into lost power at that point, either
because of a reboot or because it was unplugged. "<PWD>" means the KeyCarbon's
password was entered. By the way. the password can be changed, but the options
are somewhat limited. The password has to be seventeen characters or less, can
use only alphabetic characters and is case insensitive. Owners should make sure
to choose
something that won't be typed in accidentally. I'd recommend choosing something
like a long string of consonants. They should also be sure not to lose their password or
they will
have to send the unit back to the factory for it to be reset.
The other option for configuring the KeyCarbon and obtaining the key log is to use the KeyCarbon USB Rapid Downloader, available at the following URL:
http://www.keycarbon.com/products/keycarbon_usb/software/
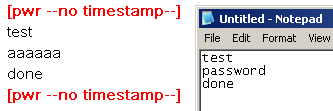
This application is much faster than the text editor option, but unfortunately the Rapid Downloader utility is only for Windows. To recover the keystrokes the owner takes the KeyCarbon unit to a Windows box where the USB Rapid Downloader is installed and then uses the menu item "Tools->Import KeyCarbon USB Log". You will notice in the screen shots below that there are two views, Normal and Raw View. Normal will be the most readable, but from time to time the user will need to look at the Raw view to see things like deletes and backspaces. Alternatively, the user can go under the "Processing Options" menu and tell it not to process edit keys.
| Normal View | Raw View |
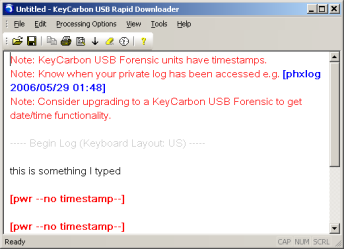 |
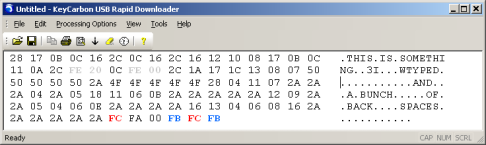 |
Another useful tweak under the "Processing Options" menu to look into is the "Hide Non-Printables" checkbox. Turning off "Hide Non-Printables" makes it easier to do a search for strings like "<LCtrl+LAlt+Del>" or "<RCtrl+RAlt+Del>" to find Windows logons. There's also "Processing Options->Tagged Words List" that allows the user to set certain keyword to be bolded and underlined for easier location.
All in all, the KeyCarbon is a neat little device and works as advertised. However, keep in mind the limitations of hardware keyloggers I stated at the beginning of this article; it may not be the best solution for all users. It's definitely worth having one in you're tool kit if your part of a tiger team. If you're doing forensic investigations however, and you decide to use a hardware keylogger instead of software, you will want to get one of BitForensics' higher end models that supports time and date stamping.
Detecting and Defeating the keylogger
I did a little Googling on detecting hardware keyloggers, and other than physical inspection there's not much information out there. As mentioned before, the KeyCarbon is not one hundred percent passive, it shows up as a generic Texas Instruments hub in the USB device list. If someone was using an asset management system to keep automated records of the hardware attached to the organizations systems this might give it away, but the admin would have to keep a watchful eye and there's likely to be some false positives. What would you think if your remote hardware audit said someone had a third part hub hooked up to their workstation? It's not the sort of thing that would raise eyebrows except amongst the ultra paranoid. As for detecting other brands of USB keyloggers, I'll have to get a few more in before I can make any definitive statements.
Since the KeyCarbon USB Mini acts as a 1.1 hub it is possible that it may be discovered if someone plugs a USB 2.0 device inline with it. Lets say for example the keyboard is plugged into a USB 2.0 hub, and the USB 2.0 hub into the KeyCarbon. If the user then plugs a USB 2.0 flash drive into the hub they may receive a warning message telling them that their thumbdrive can perform at a higher speed if they use a different port. This could lead to further investigation and the discovery of the keylogger device.
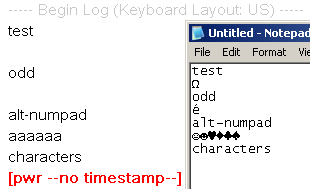
 ALT+97,
ALT+115, ALT+115, ALT+119, ALT+111, ALT+114, ALT+100 to type "password" and as
you can see from the screen shot it was not properly logged. The keystrokes just
show up as a series of "a"s in the logs. This technique for getting around the
keylogger may only work in Windows, but then Windows is also the most likely target
environment for the keylogger to be used against.
ALT+97,
ALT+115, ALT+115, ALT+119, ALT+111, ALT+114, ALT+100 to type "password" and as
you can see from the screen shot it was not properly logged. The keystrokes just
show up as a series of "a"s in the logs. This technique for getting around the
keylogger may only work in Windows, but then Windows is also the most likely target
environment for the keylogger to be used against.
I'm not sure if other USB keyloggers have this same issue, and a representative from BitForensics told me that if there are enough customer requests the logging of ALT+Numpad combos can be added in a later firmware revision.
I hope you have found this article informative. I hope to come back to the topic again once I have a few more units to test with. If you have a hardware keylogger you would like to donate to the cause please email me.
Links:
Keyloggers – content monitoring exploits
http://skrasavi.ds.uiuc.edu/Presentations/Keyloggers.ppt
Linux USB Projects Vendor and Product ID list
http://www.linux-usb.org/usb.ids
BitForensics' KeyCarbon Site
http://www.keycarbon.com/
USB View for *nix (I found this very useful for this article)
http://www.kroah.com/linux/usb/
USB View for Windows (Same name, but not a port of the Linux app
above. It's a little out of date, but still useful.)
http://www.k0lee.com/dc3000/usbts.htm
KeyMail Software Key logger
http://www.irongeek.com/i.php?page=security/keylogger

