Tracking users, malware and data leaks via the USB serial numbers on flash drives, smart phones and MP3 players
I don't write on the forensics side of security much, but I thought this was an interesting topic that I'd not seen covered much before. While I was doing my research on USB hardware key loggers I learned quite a bit about USB devices that I did not know before. Besides Vendor IDs and Product IDs, some devices also have a serial number associated with them. The “Serial Number Descriptor” string is optional, but a fair number of devices such as thumb drives, removable USB hard drives, PDAs and cell phones have them. This started me thinking: How could this data be used in a security or forensics context? I can think of a few scenarios off the top of my head:
Ω A USB flash drive is found with contraband on it, but none of the suspects claim to own it. If the serial number of the USB flash drive is found in one of suspects' Windows registry this is possible evidence as to who it belongs to.
Ω Malware has been spreading though your network, and you think thumb drives are the vector. Using the serial number you could search the network for computers where a known infected drive was used to give you an idea as to which workstations you will have to do clean up on. It may also lead you to know who brought the malware into the network (Patient Zero), or who been the biggest Typhoid Mary.
Ω You suspect some data has been stolen from a department server, and you found a suspicious MP3 player’s serial number in the Windows server's registry. MP3 players can be used as generic storage devices. By searching the network for other boxes where that same MP3 player has been plugged-in you may find that the only other box it's ever been use on is Bob's. This makes Bob a likely suspect.
I'm guessing you could come up with other scenarios where tracking a USB device’s serial number could be useful. We can see the potential, but how do we get this data, and how do we automate using it? There are two main spots you can pull this information from on a Windows XP/Vista/7 system:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\USB
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\USBSTOR
I cover both of these registry keys in more detail in my article 'Forensically interesting spots in the Windows 7, Vista and XP file system and registry' which you can find here:
http://www.irongeek.com/i.php?page=security/windows-forensics-registry-and-file-system-spots
Looking at these registry values directly is kind of cumbersome. A nicer way to look at this data is with NirSoft's freeware tool USBDeview which you can download from:
http://www.nirsoft.net/utils/usb_devices_view.html
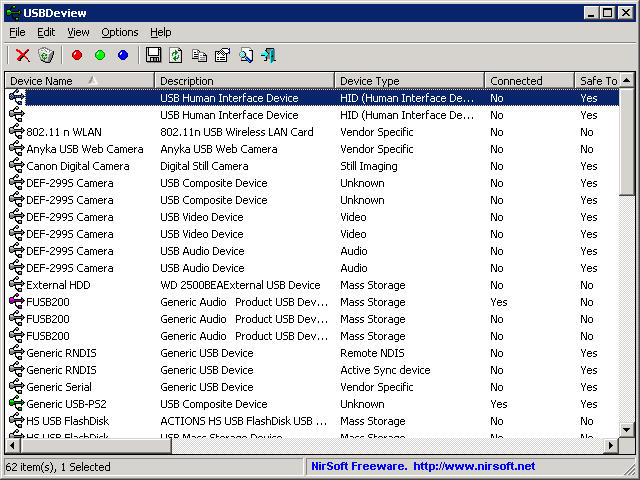
USBDeView gives the user a ton of information about what devices are currently plugged-in, and what ones have been plugged-in before but are not currently present.
Ok, now we know where on a Windows box this information is stored, but is there an automated way to find it and search our network for other locations where the same USB device has been used? Some organizations may have an asset tracking database that would be searchable for this information, but many of us don't have such a system in place. I was thinking of coding up something for the task, but I'm quite lazy. Then I remembered that most of Nir's tools have the ability to be used from across the network. Sure enough, USBDeview also had this option, all I had to do to connect to a remote Windows box and look though its registry for USB devices was to issue this simple command:
USBDeview /remote \\SomeComputer
Now keep in mind, I had to be logged in with an account that had access to that machine, and certain services have to be accessible. Nir has a nice blog post on what it takes for his tools to work from across the network:
http://blog.nirsoft.net/2009/10/22/how-to-connect-a-remote-windows-7vistaxp-computer-with-nirsoft-utilities/
That solves the problem of dumping information from one machine, but what about a whole network? Well, it seems USBDview has an option for taking a list of machines from a text file and grabbing the USB device list from all of them. The syntax is pretty simple:
USBDeview /remotefile boxes.txt
where boxes.txt is a list of computer names/IPs in UNC format. For example:
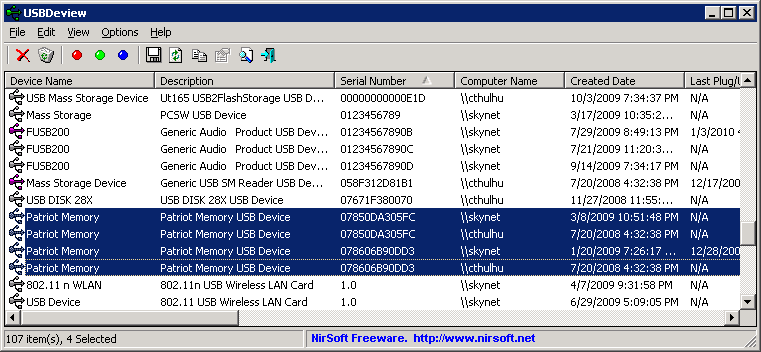
It takes a bit of time for the results to return, so be patient. Once we get the report, we can sort by the 'Serial Number' field, look for repeating serial number by eye, and then scroll over to the 'Computer Name' field to see what computers that particular USB device has been used on. For my screen shots I've reordered the columns to put the fields I'm most interested in first. The 'Created Date' and 'Last Plug/Unplug Date' fields are also usefully for figuring out a time line (really handy for finding a malware Patient Zero or Typhoid Mary based on when a user was logged on last). As you can see from the first screen shot, I have two different thumb drives from Patriot Memory that have been plugged into both my Skynet and Cthulhu workstations, but none of the other boxes I scanned:\\192.168.1.13
\\192.168.1.14
\\skynet
\\cthulhu
From the 2nd screen shot you can see that my IronKey and my former roommate’s Android Phone have only ever been plugged into my workstation named Cthulhu:
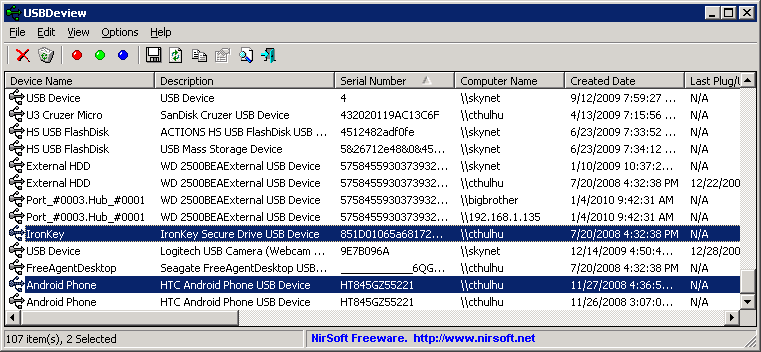
This sort of information can be erased, but local attackers rarely think of the tracks that their USB devices leave behind. I cover erasing USB track in more detail in the anti-forensics video which I will link to at the end of this article.
Now you may be thinking: sorting and looking though the table for matching USB serial numbers by hand may be fine for when you only have four workstations, but what if you have a lot more? Luckily, Nir implemented the ability to save his tool's output to many different file formats, including CSV (Comma Separated Values). Pretty much any database tool (MS Access for example) can import a CSV file, and from there you are just a few SQL queries away from finding the devices you are seeking. For example, if I wanted to look though the output for just the serial number 07850DA305FC an SQL query similar to this one may help:
SELECT Myoutput.*
FROM Myoutput WHERE Myoutput.[serial] = '07850DA305FC' ;
To dump your findings to a CSV you could take the results from the GUI, select all of the records (Ctrl-A), then choose the save icon and pick CSV from the drop down, but there is an easier way if you just intent to import the results into a database for sorting and searching. You can tell USBDeview to dump the output to a file without ever bringing up the GUI with this simple command:
USBDeview /remotefile boxes.txt /scomma myoutput.csv
With a little automation you could make regular reports. I'm still interested in finding better ways to track this sort of information, so if you know of any good free or open source asset management systems that log USB serial numbers, or are interested in coding something to help automate these types of searches, please let me know.
If you’re interested in just covering your tracks when it comes to USB serial numbers, check out my anti-forensics video:
http://www.irongeek.com/i.php?page=videos/anti-forensics-occult-computing
it's about three hours and seven minutes long, but covers a lot more than just USB devices. I hope you have enjoyed the article, and feel free to follow me on Twitter @Irongeek_ADC .
Links at a glance:
USBDeview
http://www.nirsoft.net/utils/usb_devices_view.html
What it takes for Nir's tools to work from across the network
http://blog.nirsoft.net/2009/10/22/how-to-connect-a-remote-windows-7vistaxp-computer-with-nirsoft-utilities/Forensically interesting spots in the Windows 7, Vista and XP file system and registry
http://www.irongeek.com/i.php?page=security/windows-forensics-registry-and-file-system-spotsAnti-Forensics video
http://www.irongeek.com/i.php?page=videos/anti-forensics-occult-computing


 Printable version of this article
Printable version of this article